Code signing .NET assemblies with Github Actions using Secrets
When using Github actions to build your software, you quickly find out that for .NET assemblies (at the time of writing) it seems there is nothing provided out of the box to sign your assemblies.
Several people wrote plug-ins that wrap around signtool (below is one of them too) that can be used for this process.
But how do you incorporate this into your workflow?
There are various ways to do it, almost all of them involve converting your P12 code signing certificate to base64
If you have WSL installed on your Windows box or are developing from Linux or Mac, the following command should help you converting the P12 certificate to text.
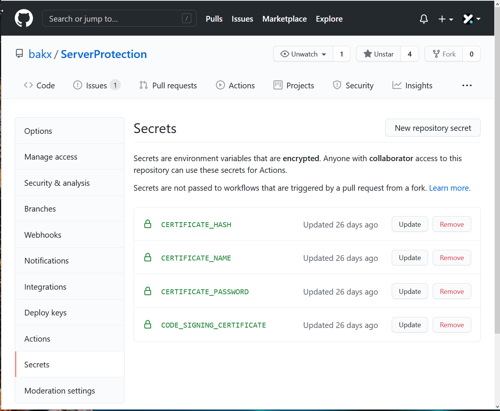
base64 -w 0 path_to_your/certificate.p12 > certificate.txtWhen you visit the Secrets page of Github actions,depending on which plug-in you use to sign you will need to enter a few fields.
The certificate and password are mandatory for all plug-ins I've seen and tested. Some also want the SHA1 hash and a name.
Using the web UI you can create these 'secrets' and enter the required values.
Note: If your password uses the ^ character, you have to escape it using ^^
If you add the following snippet into the Github actions workflow it will automatically download the plug-in and pass the values from the secrets to it
- name: Code signing SP.Core
uses: DanaBear/code-sign-action@v4
with:
# Artifact name
certificate: "${{ secrets.CODE_SIGNING_CERTIFICATE }}"
certificatesha1: "${{ secrets.CERTIFICATE_HASH }}"
password: "${{ secrets.CERTIFICATE_PASSWORD }}"
folder: SP.Core/SP.Core/bin/Any CPU/Release/net5.0/
recursive: falseSome plug-ins will only work on Windows. If you need signing on Linux, the best bet is to wait and see how .NET 5 can be leveraged.